Virtual Network
A virtual network is a network that simulates a physical network and is a combination of hardware and software network resources. A virtual network is the final product of network virtualization.
- Virtualization of the network is a method to provide virtual instances of physical networks by separating bandwidth into independent channels. Each channel can be assigned or reassigned to a specific server or device in real time and secured independently. With these combined resources, you can provision network tunnels or different segments, each with unique management and routing policies. Network virtualization is aimed at improving productivity and efficiency by performing tasks automatically, allowing files, images and programs to be managed centrally from a single physical site. Storage media, such as hard drives and tape drives, for example, can be easily added or reassigned, and storage space can also be shared or reassigned between servers. It is said that network virtualization is particularly effective in networks experiencing sudden and unforeseen increases in data and applications that consume a lot of capacity.
Virtual networks are classified into two main classes:
external and
internal.
External virtual networks consist of several local networks that the software manages as a single entity. The parts that make up the classic external virtual networks are the switching hardware and the virtual local area network (VLAN) software technology. Examples of external virtual networks include large corporate networks and data centers.
An
internal virtual network consists of a system that uses zones or virtual machines whose network interfaces are configured through at least one physical network interface card (NIC). These network interfaces are called virtual network interface cards or virtual NICs (VNICs). These zones or virtual machines can communicate with each other as if they were in the same local network and become a virtual network in a single host.
A special type of internal virtual network is the
private virtual network. Private virtual networks are different from virtual private networks (VPN). VPN creates a secure point-to-point link between two end systems. The private virtual network is a virtual network in a system to which external networks can not access. The isolation of this internal network from other external networks is achieved by configuring the VNICs using a pseudo NIC called etherstub.
How a Virtual Network Works
The following figure shows the working of a virtual network and its components in a system.
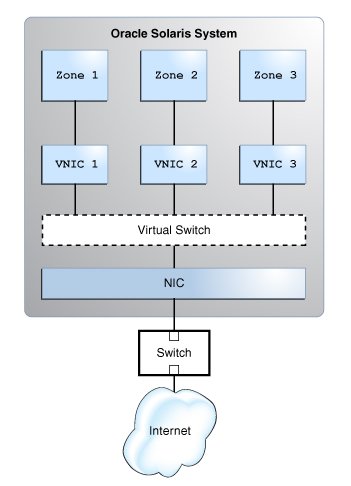
image: The figure shows VNIC configuration for a single interface.
The figure shows a single system with one NIC. The NIC is configured with three VNICs. Each VNIC is assigned to a zone. Zone 1, Zone 2, and Zone 3 are the three zones configured for use in the system. The zones communicate with each other and with the external network by using their respective VNICs. The three VNICs connect to the underlying physical NIC through the virtual switch. The function of a virtual switch is equivalent to the function of a physical switch as both provide connectivity to the systems.
When a virtual network is configured, a zone sends traffic to an external host in the same way as a system without a virtual network. Traffic flows from the zone, through the VNIC to the virtual switch, and then to the physical interface, which sends the data to the network.
The zones can also exchange traffic with one another inside the system if all the VNICs configured to the zones are part of the same VLAN. For example, packets pass from Zone 1 through its dedicated VNIC 1. The traffic then flows through the virtual switch to VNIC 3. VNIC 3 then passes the traffic to Zone 3. The traffic never leaves the system, and therefore never violates the Ethernet restrictions.
Virtual private network (VPN)
A virtual private network (Virtual Private Network, or VPN) is a technology that creates an encrypted connection through a less secure network. The advantage of using a secure VPN is that it guarantees the right level of security for connected systems when the underlying network infrastructure alone can not provide it. The rationale for using VPN access instead of a private network is usually reduced to cost and viability: It is not feasible to have a private network, for example, for a street sales representative, or it is too expensive to do so. The most common types of VPN are remote access VPNs and site-to-site VPNs.
A remote access VPN uses a public telecommunications infrastructure such as the internet to provide remote users with secure access to their organization's network. This is especially important when employees use a public Wi-Fi hotspot or other routes to use the internet and connect to their corporate network. A VPN client on the remote user's computer or mobile device connects to a VPN gateway on the organization's network. The gateway typically requires the device to authenticate its identity. Next, you create a network link to the device that allows you to access internal network resources, for example, file servers, printers, and intranets, as if you were locally on that network.
A remote access VPN usually relies on IPsec or Secure Sockets Layer (SSL) to secure the connection, although SSL VPNs often focus on providing secure access to a single application, rather than the entire internal network. Some VPNs provide Level 2 access to the destination network; These require a tunneling protocol such as PPTP or L2TP, which runs through the base IPsec connection.
A site-to-site VPN uses a gateway device to connect the entire network at one location to a network at another location, typically a small branch that connects to a data center. The end node devices in the remote location do not need VPN clients because the gateway controls the connection. Most of the site-to-site VPNs that connect over the internet use IPsec. It is also common to use MPLS carrier clouds, instead of public internet, as the VPN transport from site to site. Here, too, it is possible to have Layer 3 (MPLS IP VPN) or Layer 2 (Virtual Private LAN Service, or VPLS) connectivity running through the base transport.
VPNs can also be defined between specific computers, usually servers in separate data centers, when the security requirements for their exchanges exceed what the business network can offer. Increasingly, enterprises also use VPN connections in remote access mode or site-to-site mode to connect or connect to resources in a public infrastructure environment as a service. The new hybrid access scenarios place the VPN gateway in the cloud, with a secure link from the cloud service provider to the internal network.
PDF File:
Virtual Network, VPN - Vega, Ernesto
